Let’s discuss Step by Step Configure Intune to Kill RDP Password Saves All Endpoints. Microsoft provides a Do Not Allow Password Saving policy to control whether users can save their passwords password for Remote Desktop connection in the Remote Desktop Connection (RDC) client application.
If you Possible this policy, the “Allow me to save credentials” checkbox in the RDC client will not be available (gray), and users will be prohibited from saving their passwords RDP Session. They have to enter their credentials every time they connect.
Security Risk Mitigation is the main reason to enable this policy. If a user’s machine is lost, stolen, or compromised by malware (even if the user’s account is locked), an attacker can simply open a stored RDP connection to gain an advantage. unauthorized access to corporate network resources, potentially bypassing multi-factor authentication (MFA) if a connection is established before Ministry of Foreign Affairs session ends.
By preventing password storage, organizations ensure that users must meet any requirements dynamic authentication requirements, such as time-based One Time Password (OTP) or MFA command, for every connection, not just the first connection.
Step by Step Intune Configuration to Stop RDP Password Saving on All Endpoints
This policy is Important for data protection and regulatory compliance. The system administrator connects to the sensitive Domain Controller or Database Server must enter their credentials for each session. This ensures that access is immediately revoked if an admin workstation is compromised or left unattended, thereby preventing unauthorized access to critical infrastructure.
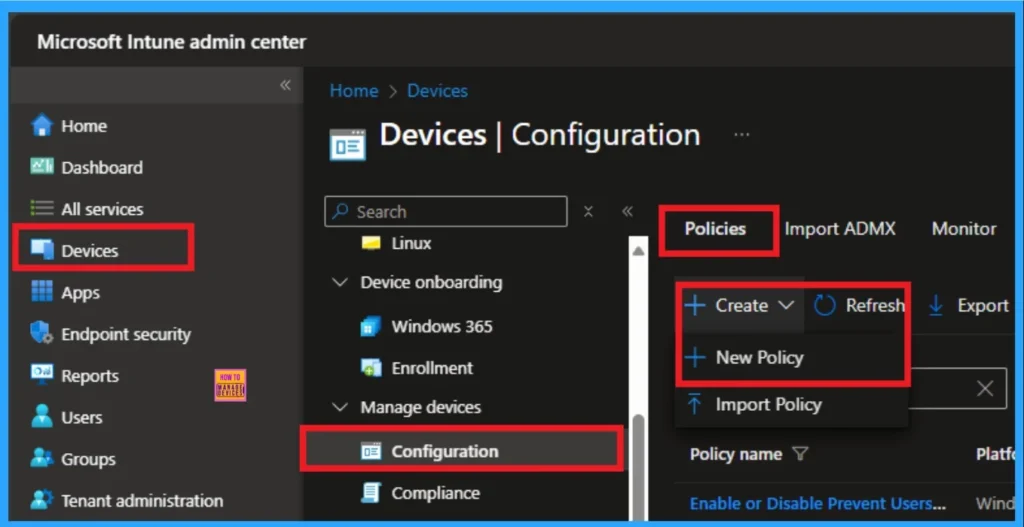
Configure Policies from the Intune Portal
This policy setting allows web-based programs to install software on a computer without notifying the user. Sign in to the Microsoft Intune Portal with Credentials. Navigate to Device > Configuration > + Create > New Policy.
Profile Selection Steps
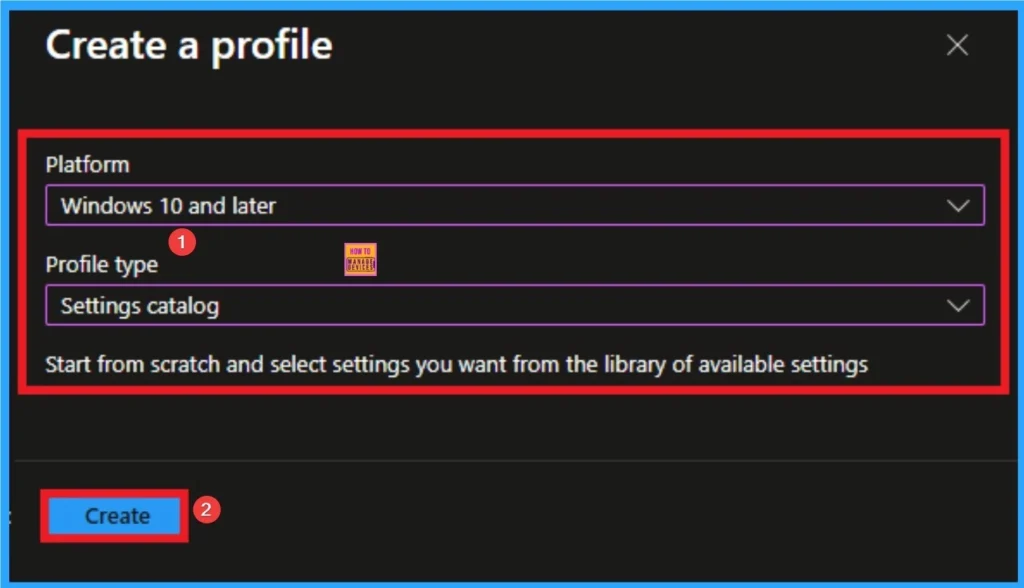
After that you can choose the appropriate one platform and profile type. This is an important step for policy creation and you cannot change the profile and platform after creating the profile. Here I want to configure the policy to be Windows 10 and newer platform catalog profiles and settings. Then click on Make knob.
Start the Policy with the Basic Tab
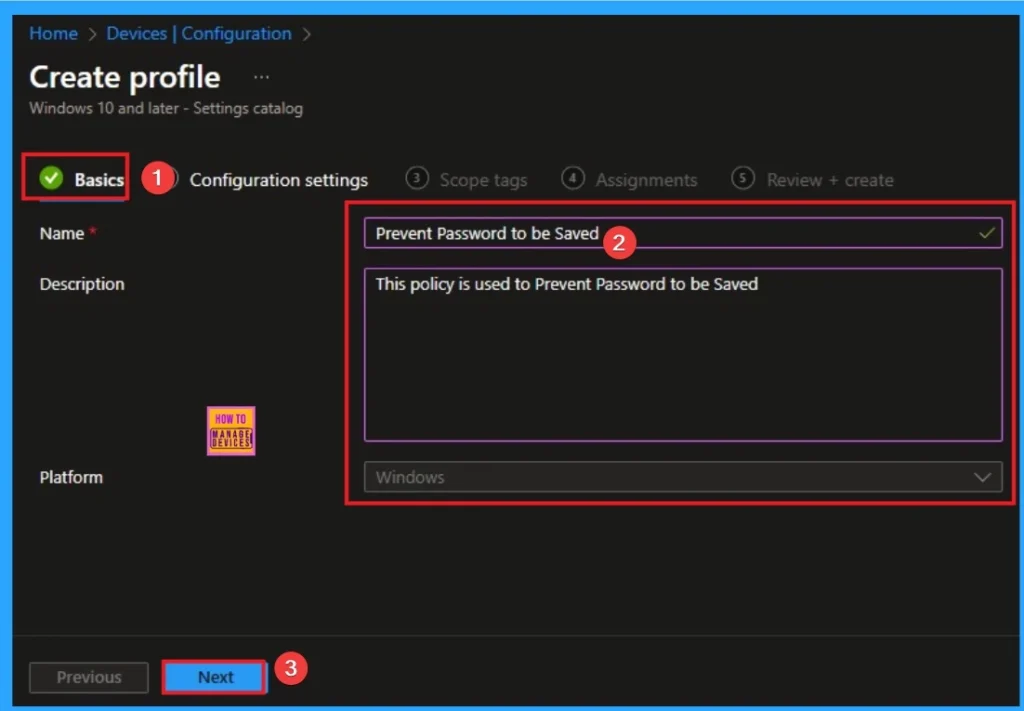
Basic Tab is the first tab that helps users provide identities for policies. For this, you can add a Name and description for the settings you want to select for policy creation. This is his name must And information is optional. After adding this click on Next knob.
Configure Cross Device Participation Policy
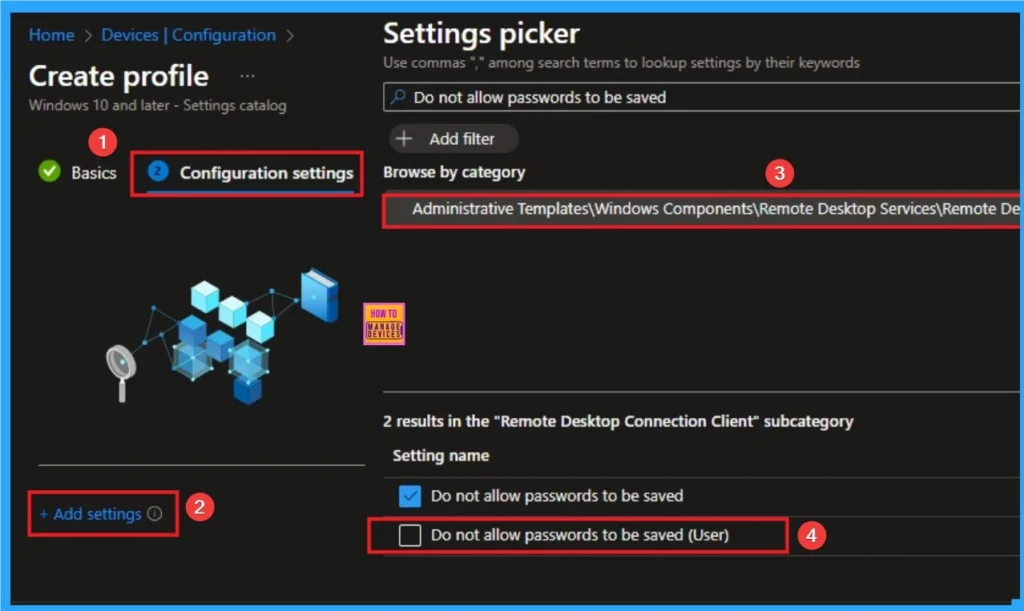
After that you will get Configuration settings tab which helps you access certain settings. To get the settings, click on +Add settings hyperlink and select a specific setting from the Settings Picker. Here, I want to select settings by browsing by Category. I choose Administrative Templates\System\Group Policies\Continue experience on this device.
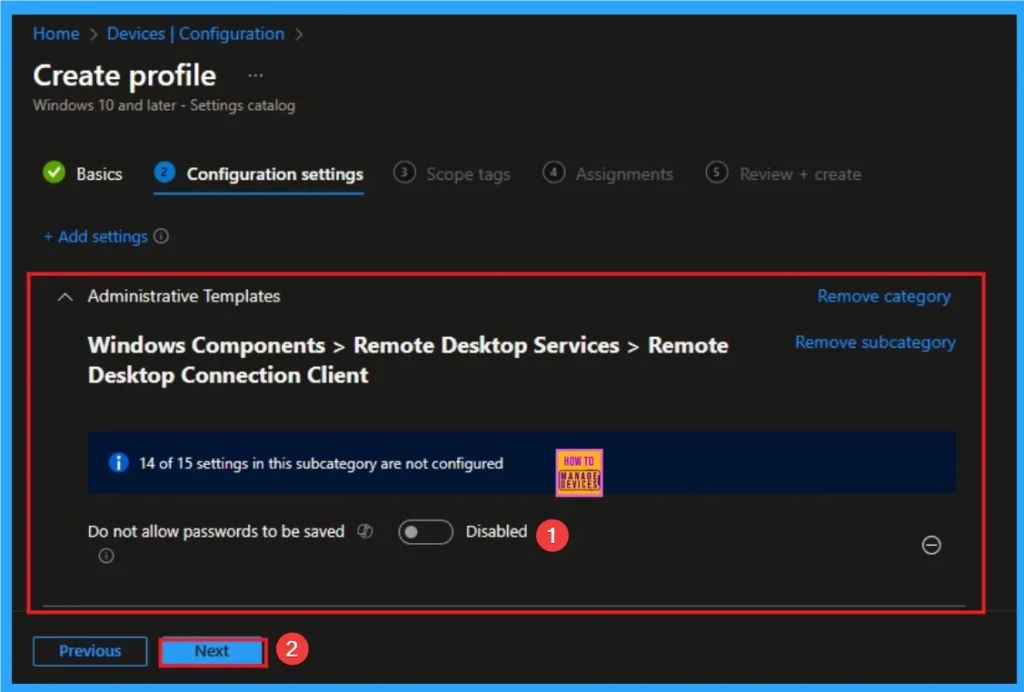
Disable RDP Password Saving
Deafly RDP Password Savings policy activated. If you want to follow this policy, click on Next knob. If not, enable the policy.
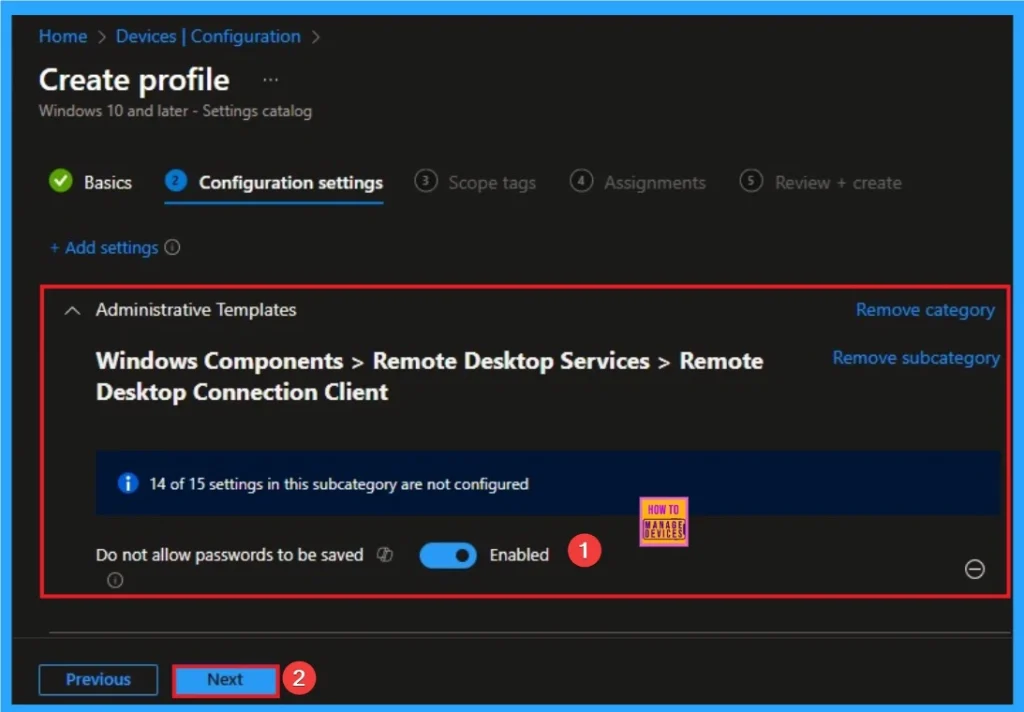
Enables RDP Password Saving
Here I want to Enable RDP Password Storage policy. So I switched the panel to the right side to enable this policy. Click on Next knob.
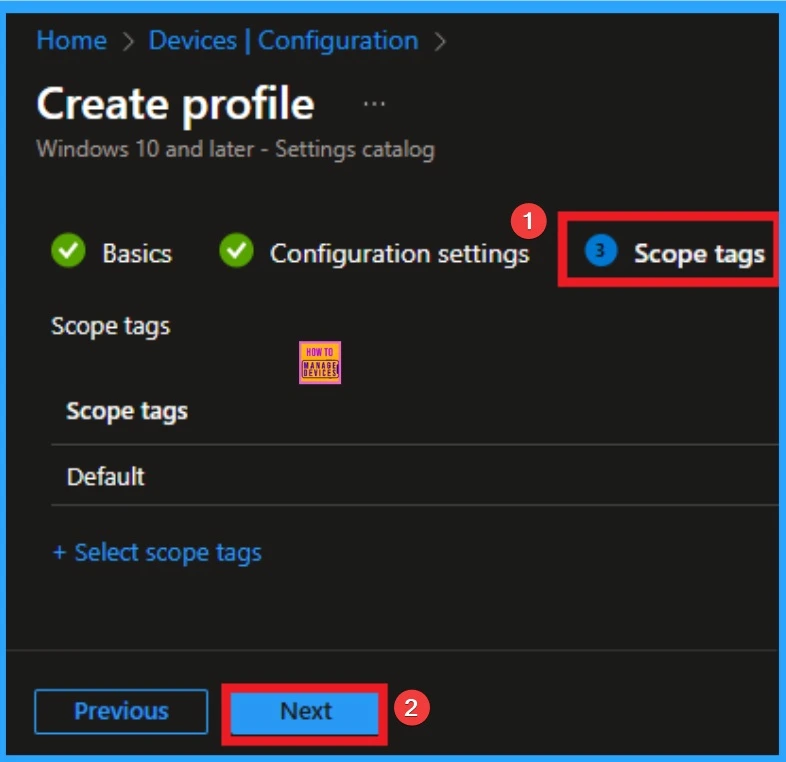
Added Scope Tag
Scope Tag is not a mandatory step in policy making. However you can add a Scope tag for visibility restrictions. Here, I didn’t add the scope tag for Company IP Range Policy. Click on Next knob.
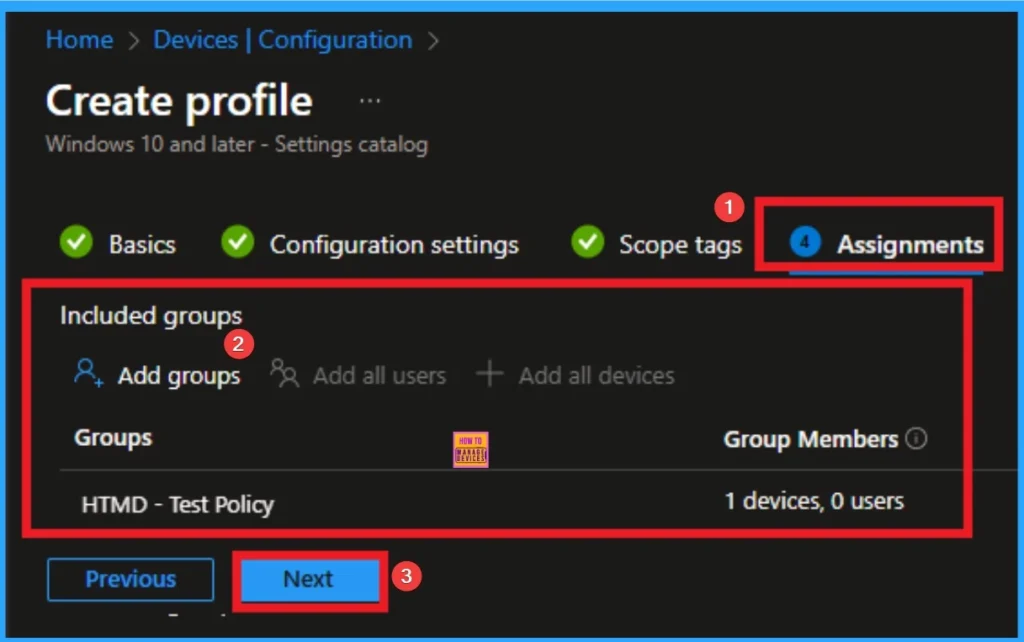
Select Groups from the Assignments Tab
To assign policies to specific groups, you can use Tasks Tab. Here I click, +Add group option under Included groups. I select a group from the group list and click Choose knob. Again, I click on Choose button to continue.
Policy Finalization
This is the final step in policy making. You can review all the details in this tab and avoid configuration errors. After verifying all the details, click Make Knob. After creating a policy, you will get a success message.
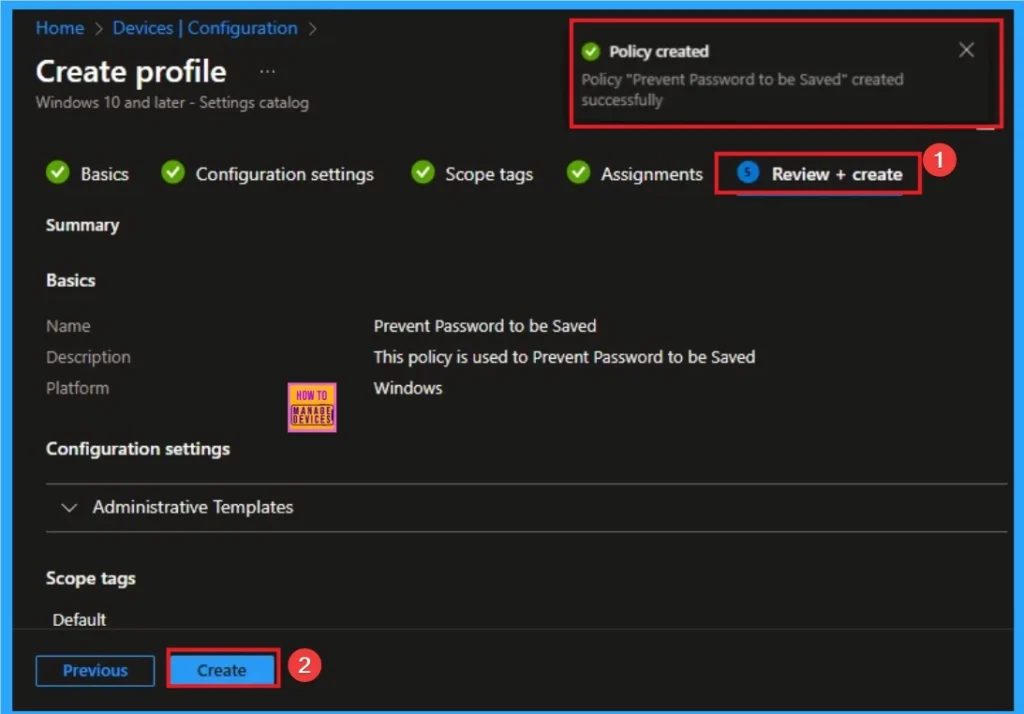
Device Check-in Status
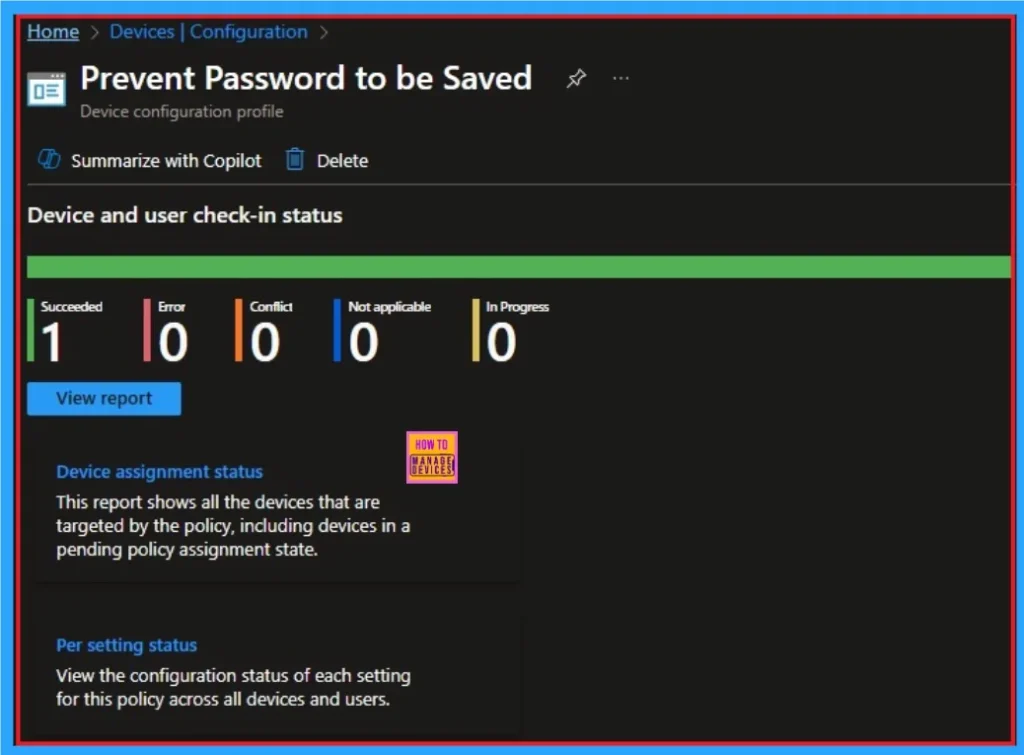
The Device Check-in Status page shows whether the Policy was successful or Not. Before checking this, you can sync devices in the Enterprise Portal for faster policy enforcement. Then Go to Device > Configuration > Search Policies. Here, the policy is shown as succeed.
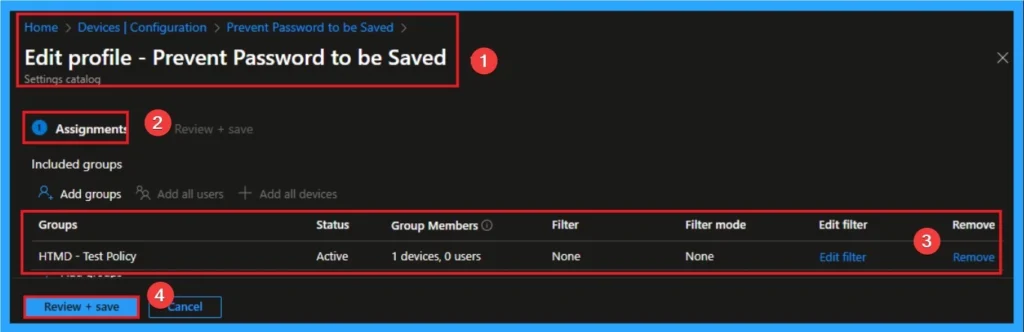
Delete an Assigned Group from Windows Cross-Device Participation Policy Settings
If you want to delete Assigned group from policy, can be from the Intune Portal. To do this, go to Policies in the Intune Portal and edit Tasks tab and Delete Policy.
To get more detailed information, you can refer to our previous post – Learn How to Delete or Unassign Apps from Intune using Step by Step Guide.
What is the Windows Cross-Device Participation Policy?
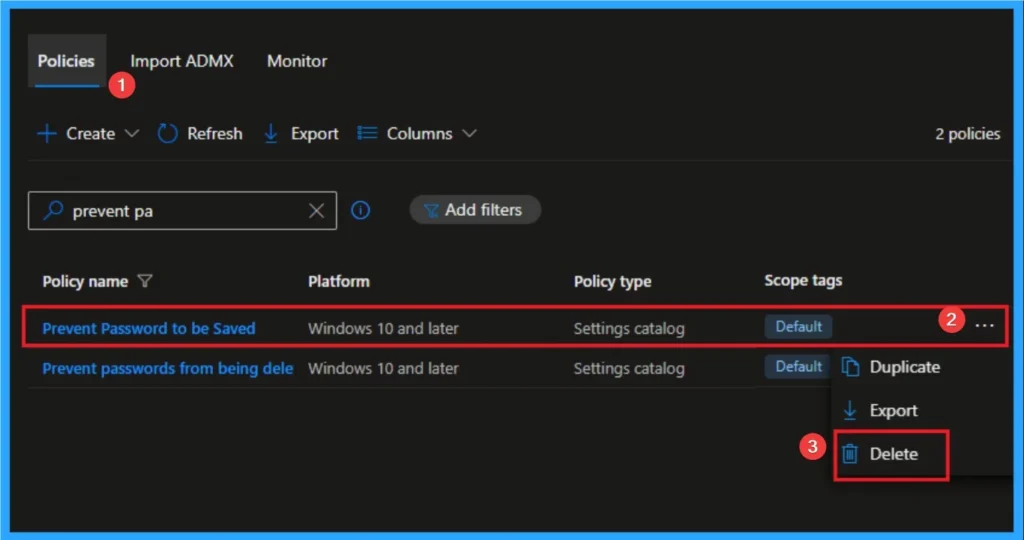
You can easily delete Policies from Intun Portal. From Configuration section, you can delete the policy. This will remove it completely from the client device.
For more information, you can refer to our previous post – How to Remove Allow Clipboard History Policy in Intune Step by Step Guide.
Need More Help or Have a Technical Question?
JoinLinkedIn page AndTelegram Groupto get step by step guides and news updates. Join usmeEtup pageto participate in User group meetings. Also, JoinWhatsApp CommunicationNityto get the latest news about Microsoft Technologies. We were thereredditas well.
Author
Anoop C Nairhas been a Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solutions Architect with over 22+ years of experience in the Workplace technology space. He is a leader of the Community of Bloggers, Speakers, and Local User Groups. The main focus is on Device Management technologies such as SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
News
Berita Teknologi
Berita Olahraga
Sports news
sports
Motivation
football prediction
technology
Berita Technologi
Berita Terkini
Tempat Wisata
News Flash
Football
Gaming
Game News
Gamers
Jasa Artikel
Jasa Backlink
Agen234
Agen234
Agen234
Resep
Cek Ongkir Cargo
Download Film



