Let’s discuss Solve problems and fix devices that are not visible to the defender for business after intune onboarding. Microsoft Intune users who face problems when the onboarding device through the onboarding intune script and local does not appear on the Microsoft Defender portal.
Users follow the necessary instructions provided by Microsoft. The device is not displayed in Microsoft Defender portal. Local onboarding script method and directly through intune. The user is confused, is there conflict run both.
For onboarding devices, the user used to carry out these tasks is a Global Admin (even with security administrator rights). In connection with Intune, the connection service between intune and defender for the end point (EDR) is fine.
The main reason for this problem is Conflict between onboarding methods And misalignment of compliance policies. As mentioned above the user applies 2 onboarding methods, such as local onboarding scripts, and EDR policies that have been previously configured through intunes that lead to conflict.

Solve problems and fix devices that are not visible to the defender for business after intune onboarding
As mentioned, users also follow the EDR policy options that were previously configured for the device. This dual approach can cause an inconsistent registry or telemetry entry, prevent the device to register properly on the defender portal.
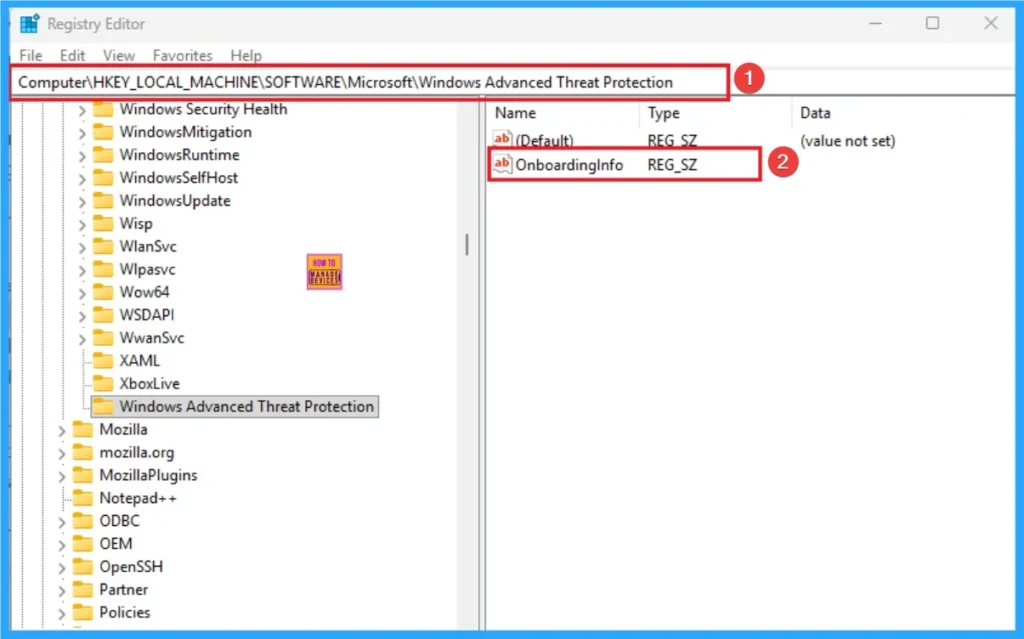
The device is displayed as obedient in Intune, but there is a underlying problem: “Having a compliance policy assigned”. Create a local admin user account “policy conflict. The table below shows the registry key used to check which states of onboardinginfo, which shows that the device is in Microsoft Defender for the end point.
| Registry key |
|---|
| Hklm \ software \ policy \ microsoft \ windows advanced threat of protection |
After the effect effect
Devices that are not displayed in the average telemetry defender are no warnings, no threat detection, no automatic response. The security team can consider the device to be protected when not, leaving a blind point in the protection of the end point. Conditional access and other security policies that rely on defender signals cannot trigger properly.
Solution
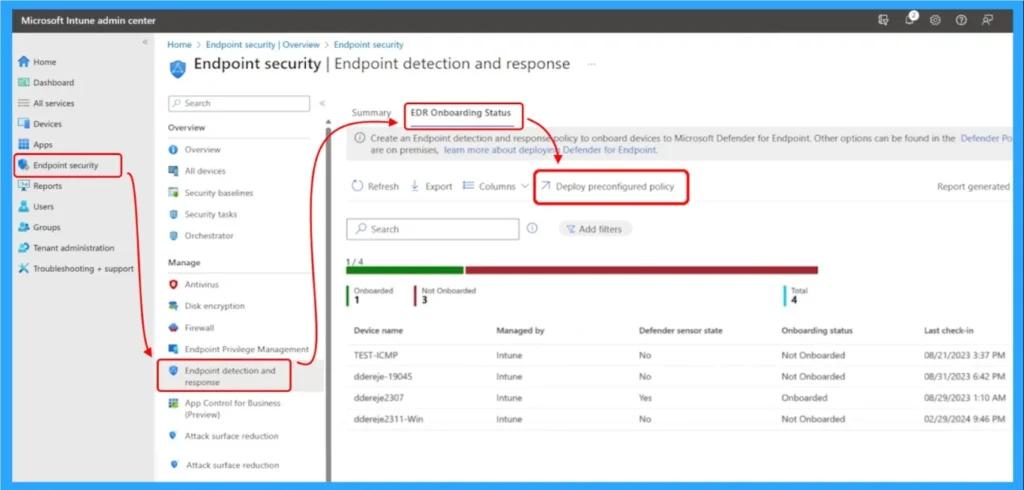
You can follow the Severla problem solving method to solve this problem. You can try methods such as avoiding the use of both orientation methods, trying onboarding new devices, run the MDE connection analysis tool.
- Avoid using both onboarding methods (script + EDR policy) simultaneously can cause conflict.
- Try onboarding a new device using only one method to isolate this problem.
- Run the MDE connection analyzing tool – this helps diagnose connectivity and orientation problems.
- Create a custom compliance policy – help to cut problems with default policies.
Need further assistance or have technical questions?
JoinLinkedIn page AndTelegram GroupTo get a step -by -step guide and news renewal. Join usMeeting pageto participate in the user group meeting. Also, joinWhatsApp communityTo get the latest news about Microsoft Technologies. We were thereRedditas well.
Author
Anoop C Nairhas been Microsoft MVP for 10 consecutive years from 2015 and so on. He is an architect of workplace solutions with more than 22 years of experience in workplace technology. He is a blogger, speaker, and leader of the local user group community. The main focus is on device management technology such as SCCM and Intune. He wrote about technology such as intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
Game Center
Game News
Review Film
Berita Olahraga
Lowongan Kerja
Berita Terkini
Berita Terbaru
Berita Teknologi
Seputar Teknologi
Berita Politik
Resep Masakan
Pendidikan
Berita Terkini
Berita Terkini
Berita Terkini
review anime



