Today we discuss the Policy for Securing SME Communications with Intune Using Digital Signatures. This policy ensures that file sharing on Windows computers always occurs protected. This forces the system to use so-called digital security checks signing whenever data is sent or received using SMB (file and printer sharing).
This means the computer will not receive or send data unless the connection is secure. SMEs generally used in office to share filesfolders, and printers. Because this data travels over the network, it can be targeted by attacker if not protected.
Without this setting, someone on the same network could try to read or change the data while it is in progress transferred. By enabling this SMEs policy, the computer checks every message it sends or receives. If the message is altered or comes from an untrusted source, then connection stopped. This helps keep company data safe and secure prevent Wrong.
In Intune, these policies are implemented by creating configuration profiles and choose the settings Microsoft network server: Digitally sign communications (always) from Security Options. Once activated and set, Intune automatically applies this protection to all selected devices.
Securing SMB Communications with Intune Using Digital Signature Communications Policies
After the policy is implemented, window will only communicate with other computers that also support secure SMB signing. This gets in the way not safe or outdated systems that don’t keep up modern security rule. The biggest profit This policy is a protection against hacking attempts such as sessions piracy. This ensures that no one can secretly change data or pretend to be a trusted computer on network.
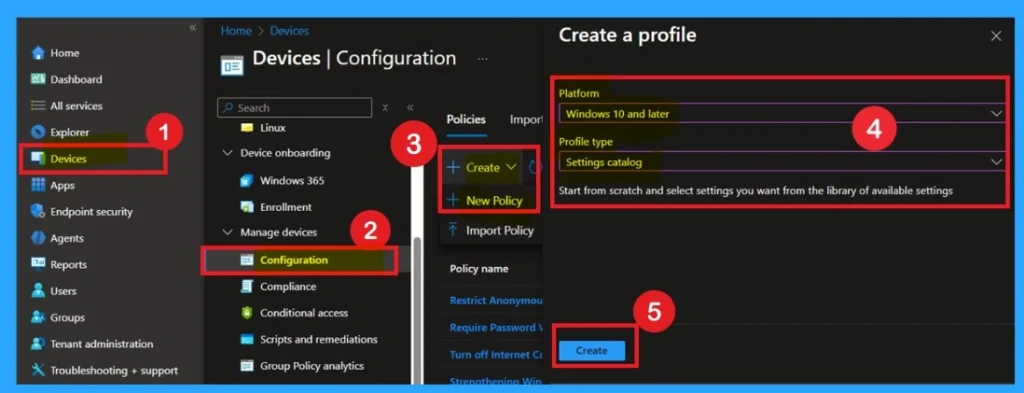
Create a Profile
To get started, open it Microsoft Intune and log in with your administrator credentials. Once logged in, navigate to the Devices section and select it Configuration Profile. In this section, click + Create Policies option to create a new configuration profile.
- The new window is titled Create a Profile will appear.
- Here, you need to provide some basic details: for Platform, select Windows 10 and later, and for Profile Typechoose Settings Catalog.
- After selecting this option, proceed to create a profile.
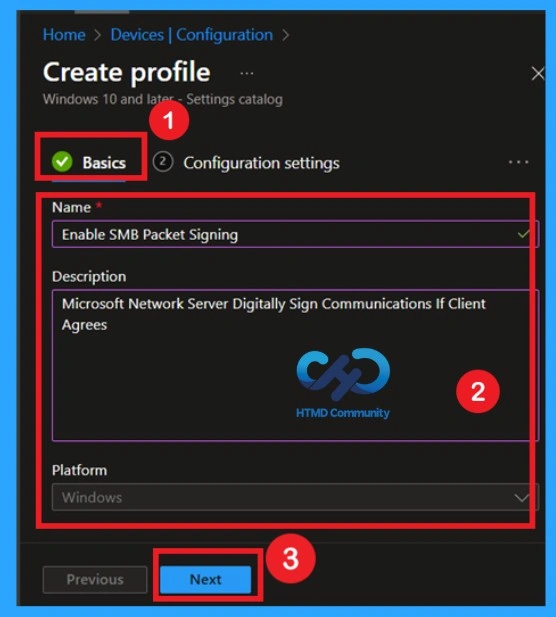
The Importance of Basics
Now, we all know what it is Base tabs matter to us. Otherwise, it simply refers to the first step in the policy creation process, where you provide basic details of your policy. In this section, you must enter important information like Name And Information of that policy. You can give any name to the policy so that it helps you identify it easily later.
| Basic Details | Information |
|---|---|
| Name | Possible SMEs Package Signing |
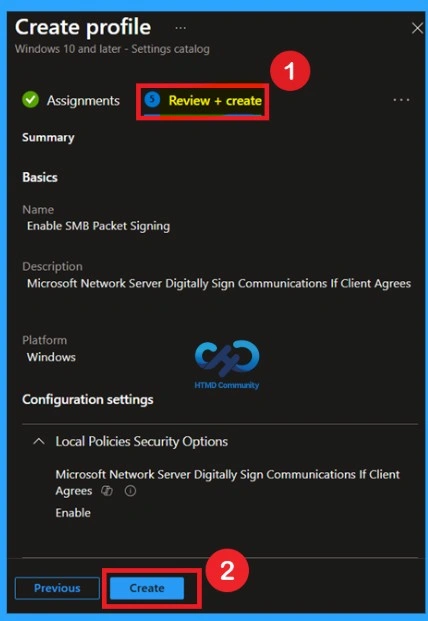
| Information | Microsoft Network Server Digitally Signs Communications If Client Agrees |
| Platforms | window |
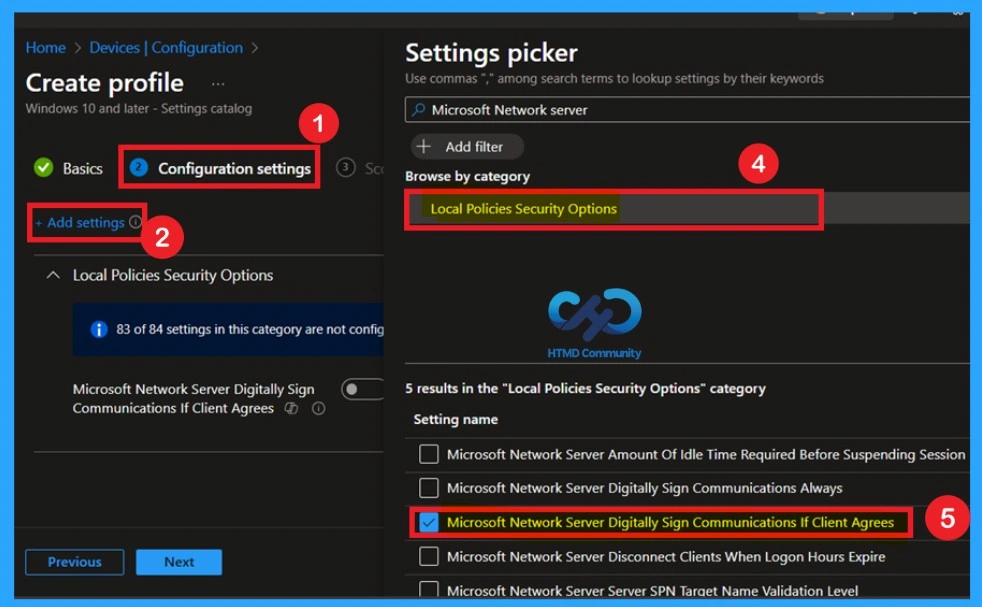
Configuration Settings
Now you are in Configuration settings page from profile; here, click + Add settings to open the Settings selector window, then browse by category and select Local Policy Security Options, Find the Microsoft Network Server Digitally Sign Communications If Client Agrees setting, select the check box next to it, and close the Settings selector to add the policy to your configuration.
Policy Mode Disabled
After selecting a policy, you can now close ite Settings Selector window. You will be returned to the Configuration Settings page, where you can see that the policy is currently set With disabilities by default. If you want to continue without making any changes, just click Next to continue.
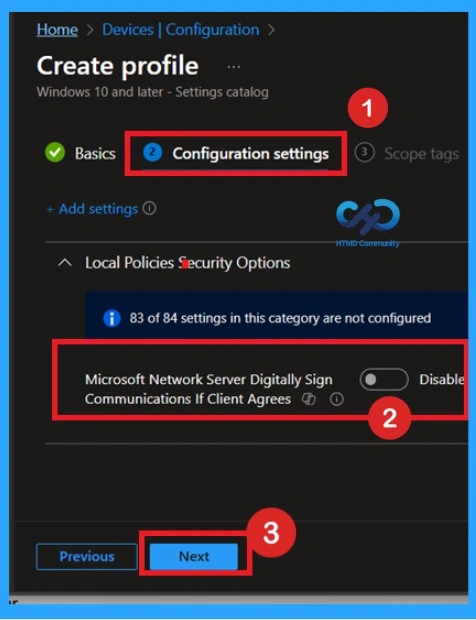
Enable Policy
In Configuration settings page, find the Microsoft Network Server: Digital Signature Communications If Client Agrees policy under Local Policy Security Options, turn the dial to Enabledthen click Next to continue setting up the profile.
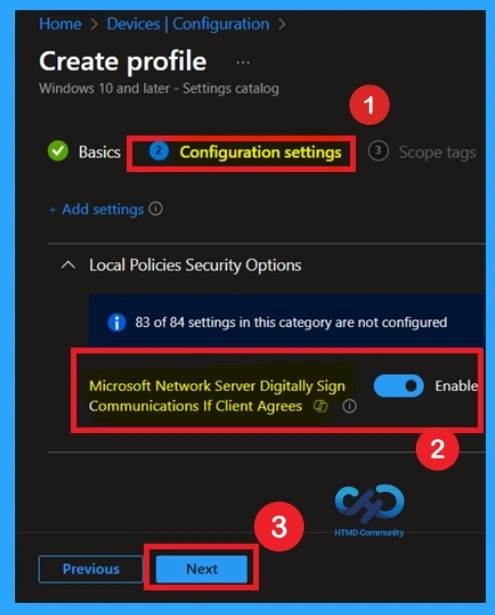
That scope tag is not mandatory, so you can skip this part. It serves as a tool for organization and access management, but assigning it is optional. Click Next if it is not necessary for your setup.
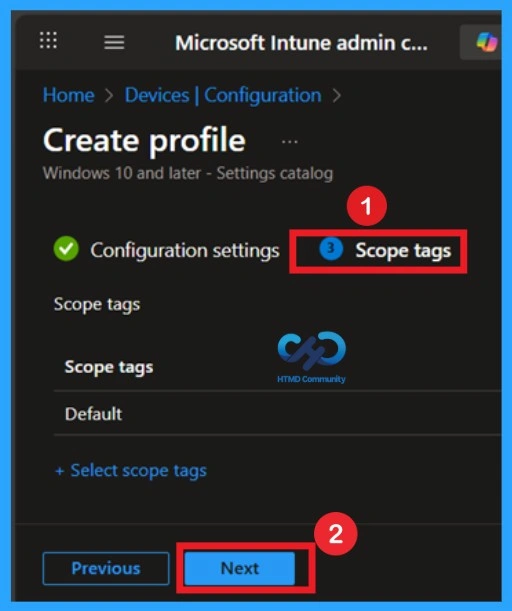
Assignment Section
That Assignment this section is very important for policy spread. In this section, you decide who will receive the inside policy organization. If you want to target certain groups, users, or devices, you can add them here to ensure the policy only applies to the intended audience.
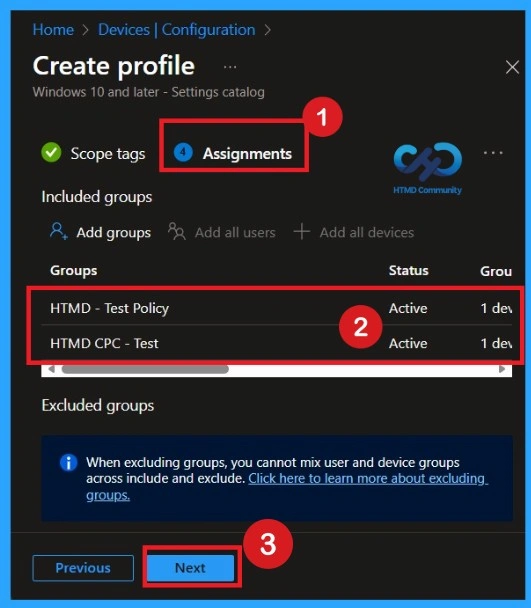
Review + Create
Review + Create is the final stage of policy making. In this step, you will see a summary of all the details, including Basics, Configuration Settings, Taskand much more. You can review them all informationand if anything needs to be changed, you can go back to the previous step and edit them easily.
Monitoring Details
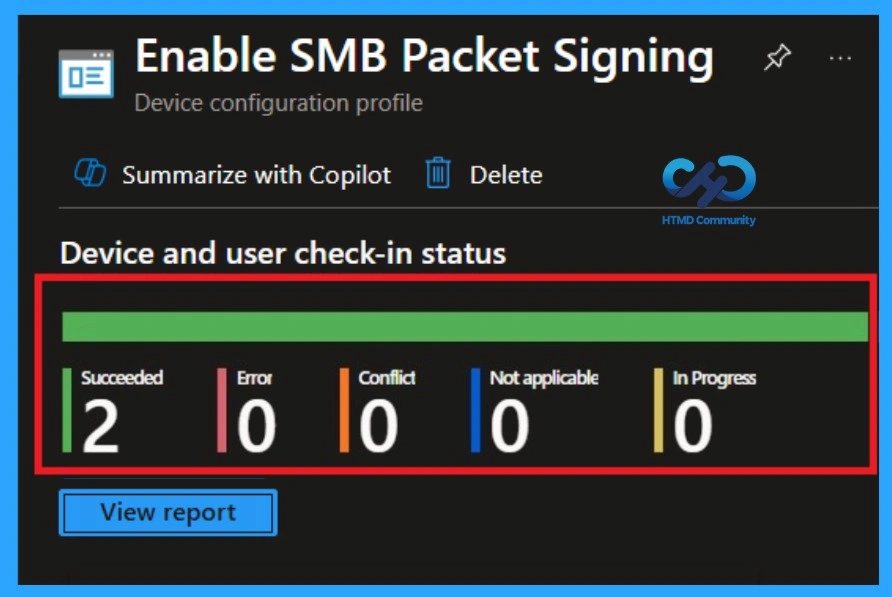
After creating a policy, you may wonder if this is indeed the case succeed implemented or not. It is very important to verify this. To check it, you usually need to wait until 8 hours so that the policy can be implemented synchronize automatically. However, if you want faster results, you can synchronize manually the policy through the Company portal
- Navigate to Device > Configuration Policy.
- In Configuration Policy register, search for the policy you created.
- Click on a policy to view it implementation status and details.
How to Delete a Policy
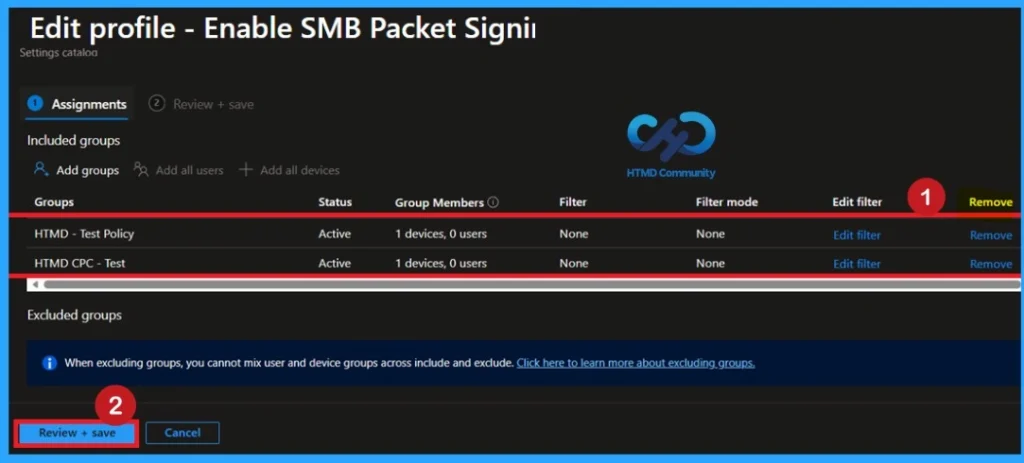
After creating a policy, if you wish delete the group you previously selected, you can do it easily. First, go to Device > Configuration policies. In the Configuration policies section, look for the policy, In the Your When policy section Scroll down page, and you will see a section like Basic Details and Assignment Details.
- In Task sectionYou will find Edit option and click on it.
- When you click Edit, you will go to Assignment page.
- Click Deletethen continue by clicking Review + Save.
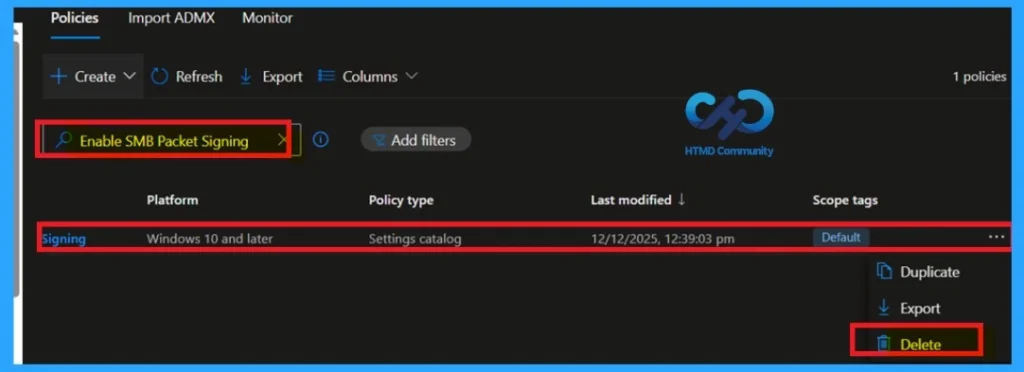
How to Delete a Policy You Created
To delete a policy in MS Intune, first go to Microsoft Intune Admin Center. Navigate to Devices and select it Configuration. Search for and select the specific policy you want delete. Once you are on the policy details page, click three dot menu in the top right corner and select Delete from the available options.
End User Results
Once this configuration is implemented, end users will not notice any noticeable changes in their daily work. They can continue enter, access files, and use network resources as usual without disturbance. This policy works silently in the background and does not affect normal conditions. authenticated user activity.
Need More Help or Have a Technical Question?
JoinLinkedIn Page AndTelegram Groupto get step by step guides and latest news updates. Join usMeeting Pageto participate in User group meetings. Also, join inWhatsApp Communityto get the latest news about Microsoft Technologies. We were thereredditas well.
Author
Anoop C Nairhas been a Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solutions Architect with over 22+ years of experience in the Workplace technology space. He is a leader of the Community of Bloggers, Speakers, and Local User Groups. The main focus is on Device Management technologies such as SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
News
Berita Teknologi
Berita Olahraga
Sports news
sports
Motivation
football prediction
technology
Berita Technologi
Berita Terkini
Tempat Wisata
News Flash
Football
Gaming
Game News
Gamers
Jasa Artikel
Jasa Backlink
Agen234
Agen234
Agen234
Resep
Cek Ongkir Cargo
Download Film


