Let’s discuss how to prevent it Client Printer Mapping in a Remote Desktop Services Session using Intune. This policy setting controls whether users connect to a Remote Desktop Session Host (RD Session Host) the server (or a Virtual Desktop Infrastructure/Cloud PC environment such as Azure Virtual Desktop or Windows 365) is allowed to use printers installed on its local/client computers in a remote session.
By enabling this policy, the number of temporary cases or unknown printer object created on a remote host, resulting in a cleaner and more predictable server environment. Thus avoiding the need to implement and manage more complex ones centralized printing solution (such as a dedicated print server or Microsoft Universal Print).
This policy also prevents potential crashes or instability in RD Session Host server is caused by being incompatible or poorly written client printer the driver is loaded into the server’s print spooler. This is a common historical problem.
With this policy the admin can provide smooth running user experiencebecause the local printer automatically appears in the remote session. Organizations must decide strategically whether security and stability benefit from it possible the policy outweighs the loss of printing convenience for its users.
How to Prevent Client Printer Mapping in Remote Desktop Services Sessions using Intune
Let me explain the implementation of this policy with an Example. Financial services companies use virtual desktop environments (e.g., Azure Virtual Desktops or traditional RDS farms) for handling employees confidential client data (e.g., investment portfolio, social security number.
Configure Policies from the Intune Portal
Sign in to the Microsoft Intune Portal with Credentials. Navigate to Device > Configuration > + Create > New Policy.
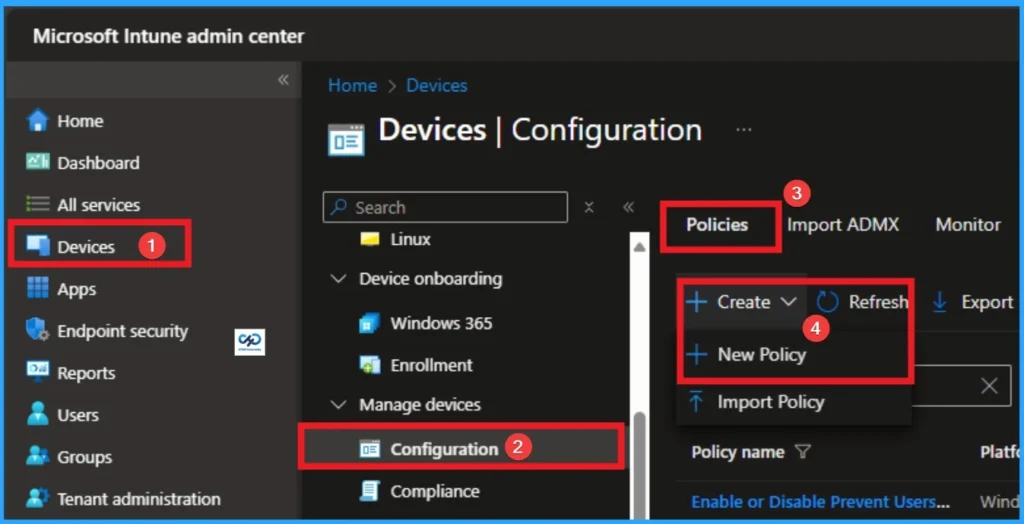
Profile Selection Steps
After that you can choose the appropriate one platform and profile type. This is an important step for policy creation and you cannot change the profile and platform after creating the profile. Here I want to configure the policy to be Windows 10 and newer platform catalog profiles and settings. Then click on Make knob.
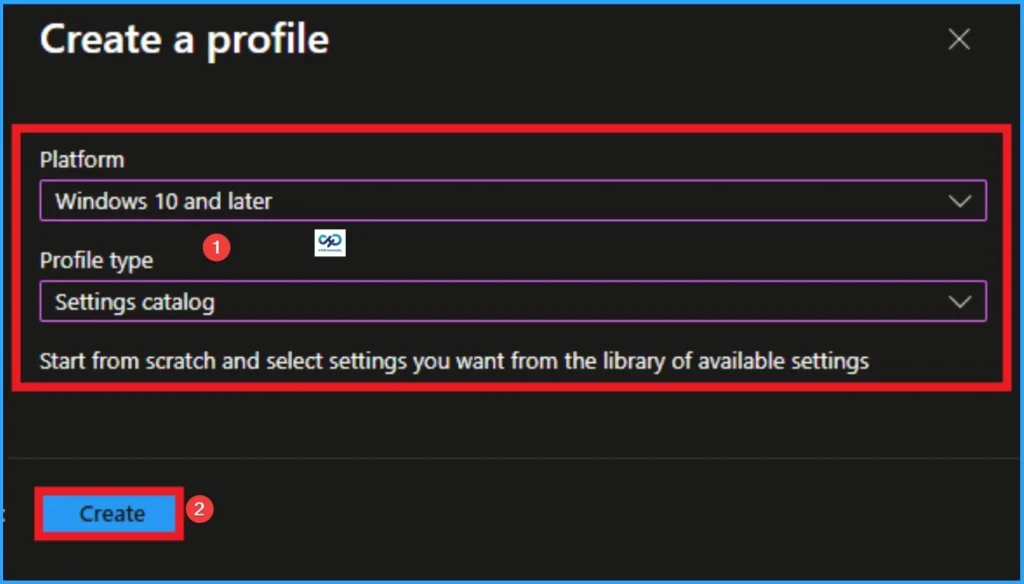
Start the Policy with the Basic Tab
Basic Tab is the first tab that helps users provide identities for policies. For this, you can add a Name and description for the settings you want to select for policy creation. This is his name must And information is optional. After adding this click on Next knob.
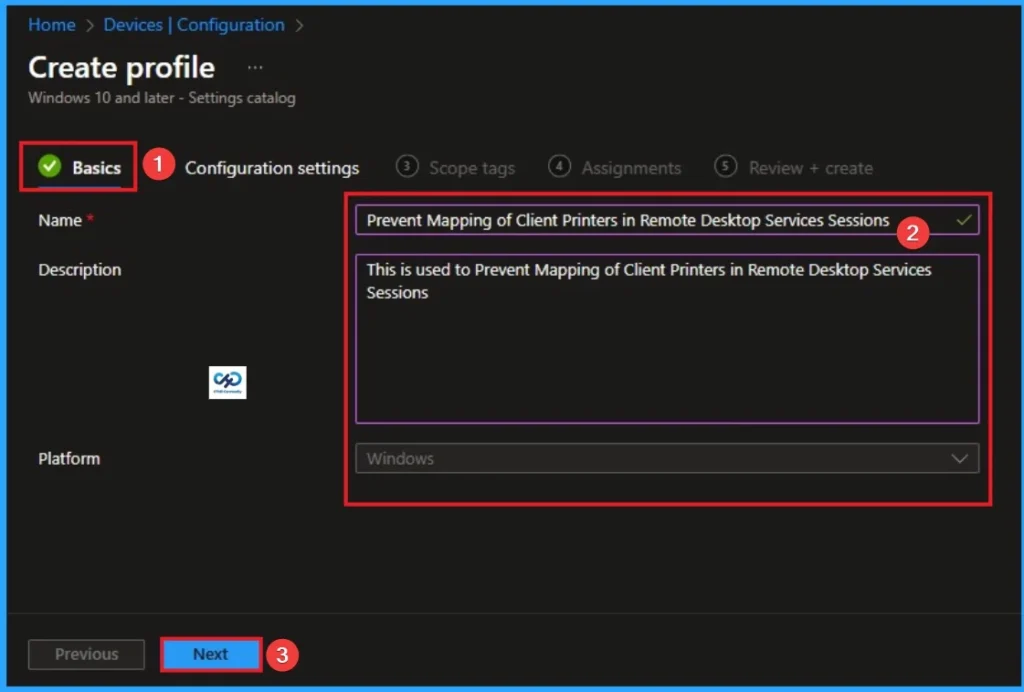
Configure Cross Device Participation Policy
After that you will get Configuration settings tab which helps you access certain settings. To get the settings, click on +Add settings hyperlink and select a specific setting from the Settings Picker. Here, I want to select settings by browsing by Category. I choose Windows Components > Remote Desktop Services > Remote Desktop Session Host > Printer Redirection >Do not allow client printer redirection.
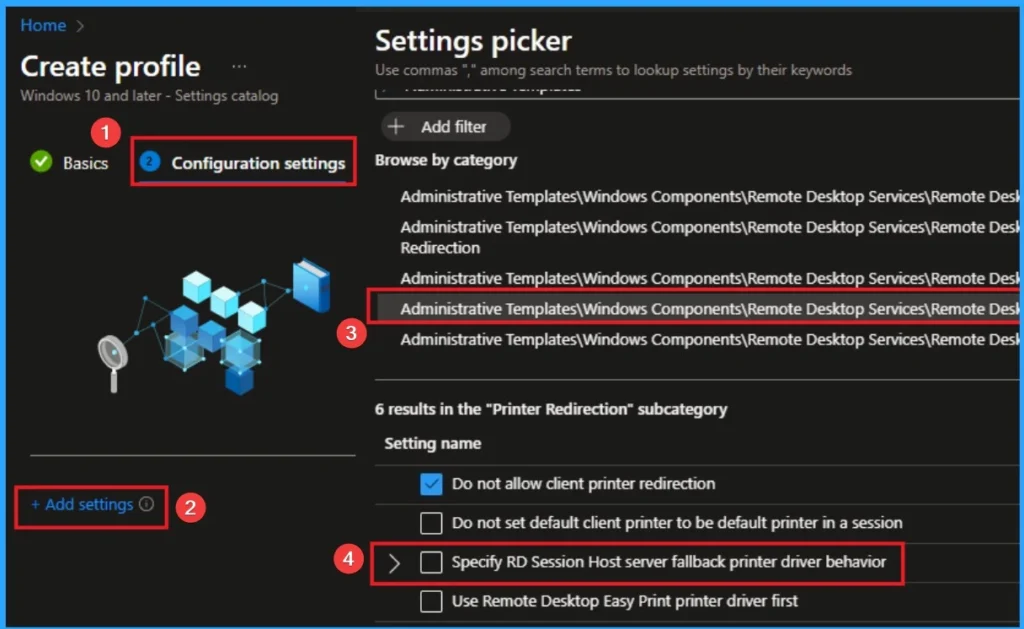
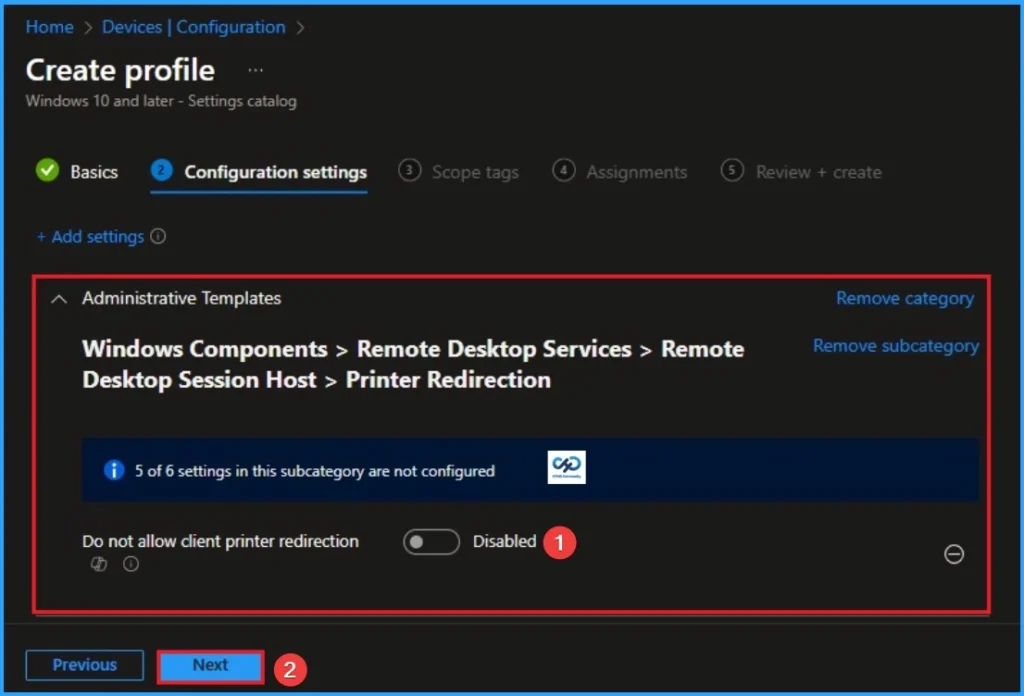
Disable Client Printer Mapping in Remote Desktop Services Sessions
If you disabled these policy settings, users can redirect print work with client printer mapping. By default, this policy is disabled. Click on Next knob.
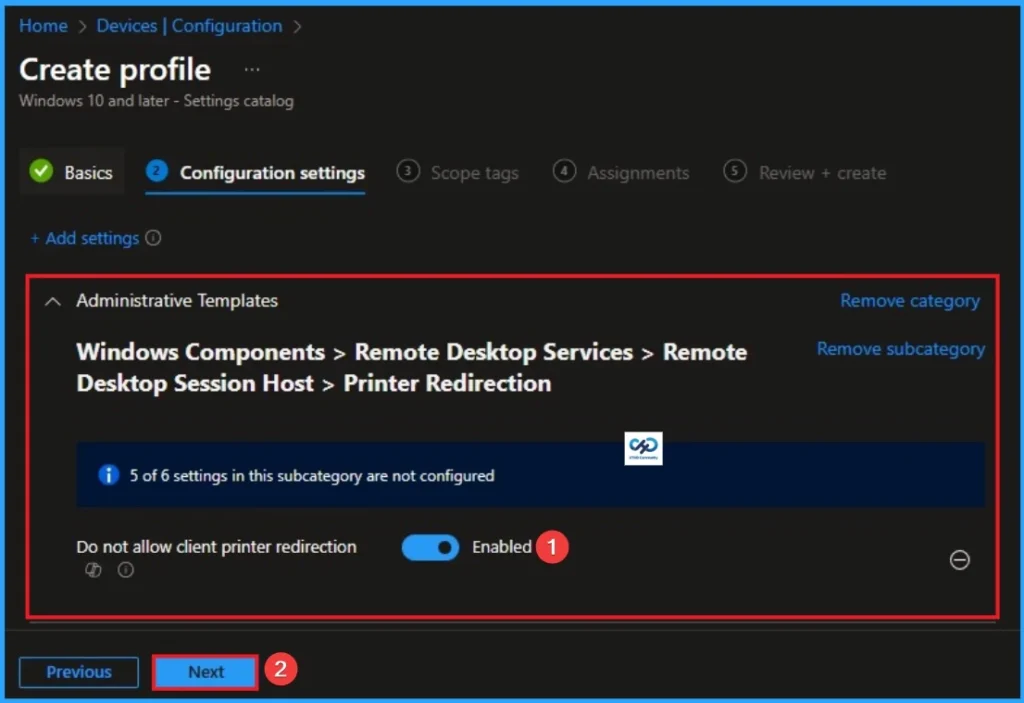
Enable Client Printer Mapping in Remote Desktop Services Session
If you enable this policy setting, users cannot redirect print jobs from a remote computer to a local client printer in a Remote Desktop Services session. Click on Next knob.
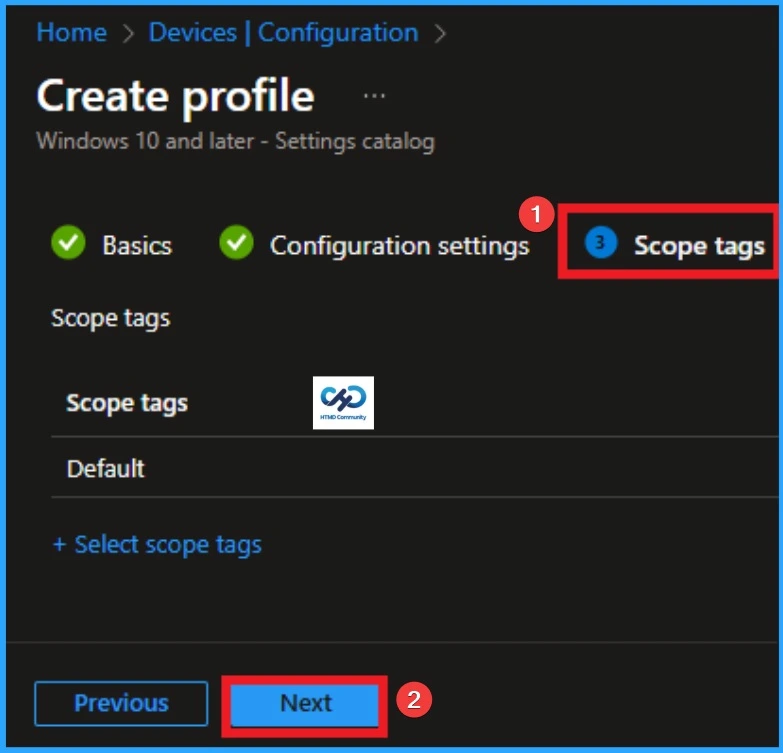
Added Scope Tag
Scope Tag is not a mandatory step in policy making. However you can add a Scope tag for visibility restrictions. Here, I didn’t add the scope tag for Prevent Client Printer Mapping Policy. Click on Next knob.
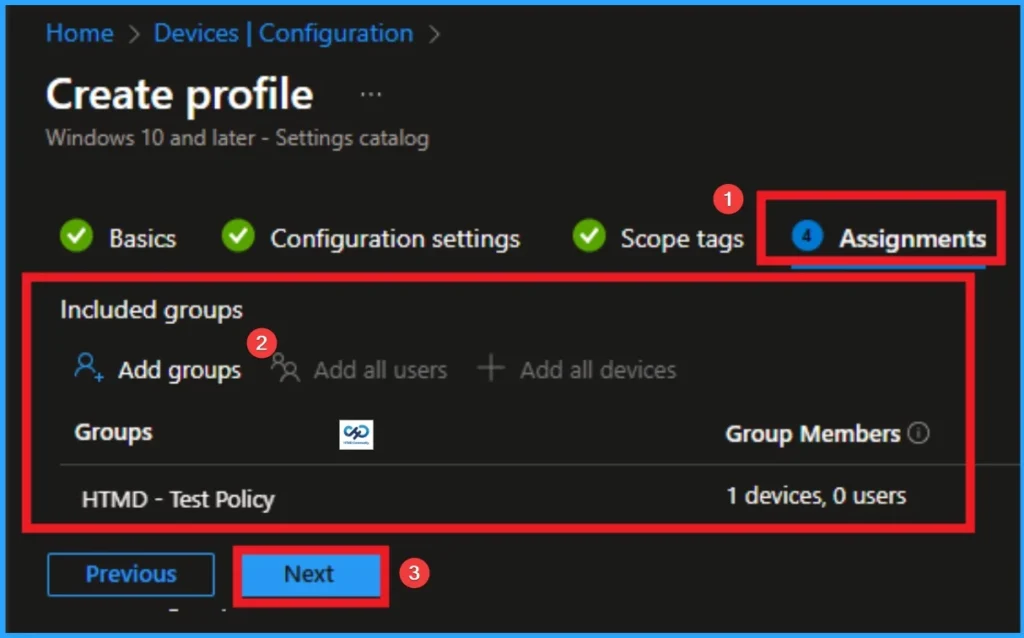
Select Groups from the Assignments Tab
To assign policies to specific groups, you can use Tasks Tab. Here I click, +Add group option under Included groups. I select a group from the group list and click Choose knob. Again, I click on Choose button to continue.
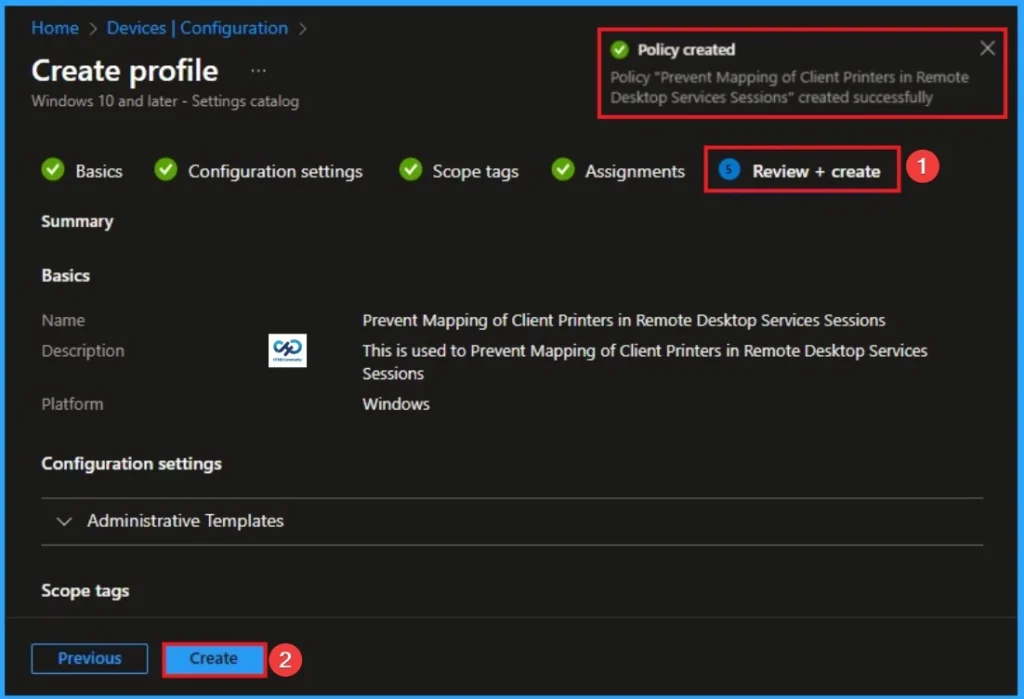
Policy Finalization
This is the final step in policy making. You can review all the details in this tab and avoid configuration errors. After verifying all the details, click Make Knob. After creating a policy, you will get a success message.
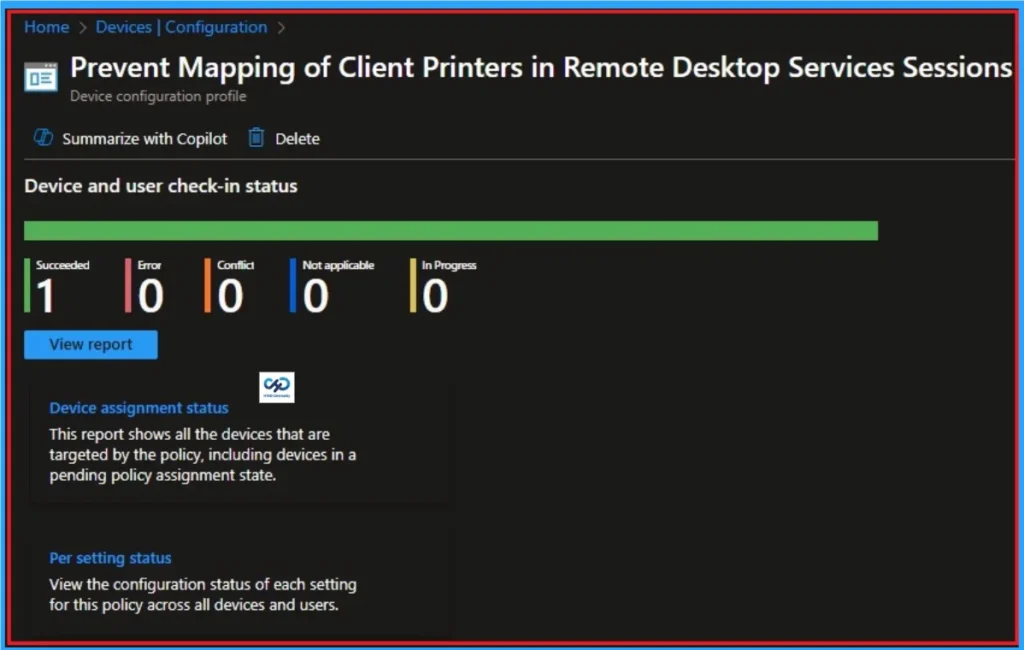
Device Check-in Status
The Device Check-in Status page shows whether the Policy was successful or Not. Before checking this, you can sync devices in the Enterprise Portal for faster policy enforcement. Then Go to Device > Configuration > Search Policies. Here, the policy is shown as success.
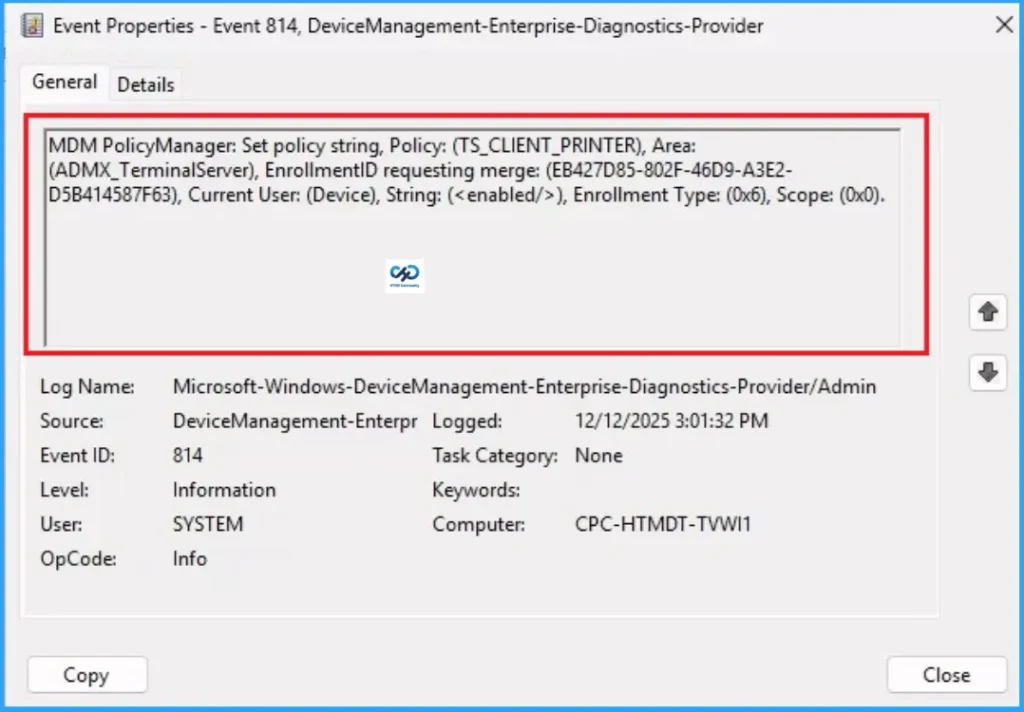
Client Side Verification
To confirm the policy success or not, you can use Event Viewer. First, open Event Viewer and navigate to Application and Service Logs > Microsoft > Windows > Device Management > Enterprise Diagnostics Provider > Admin. Search for Event ID 813 or 814, as this usually contains policy-related information
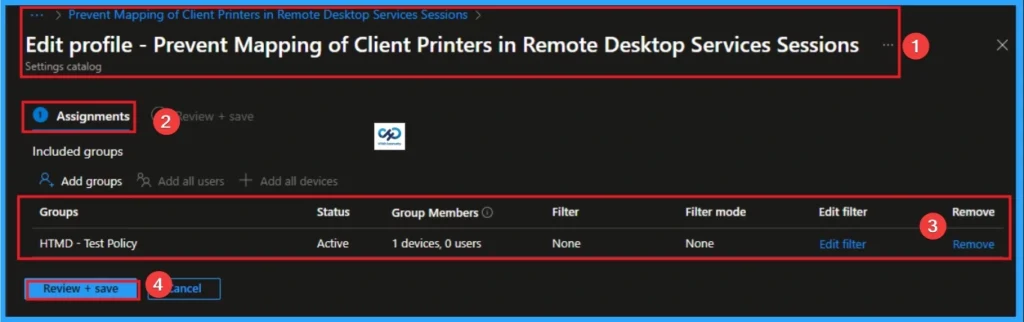
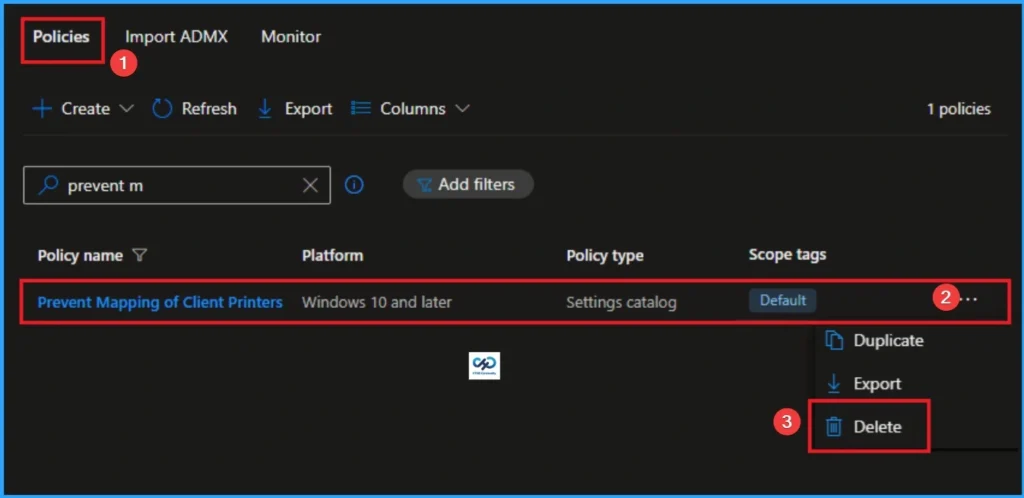
Delete an Assigned Group from Prevent Mapping of Client Printer Policy Settings
If you want to delete Assigned group from policy, can be from the Intune Portal. To do this, go to Policies in the Intune Portal and edit Tasks tab and Delete Policy.
To get more detailed information, you can refer to our previous post – Learn How to Delete or Unassign Apps from Intune using Step by Step Guide.
How to Remove the Prevent Client Printer Mapping Policy
You can easily delete Policies from Intun Portal. From Configuration section, you can delete the policy. This will remove it completely from the client device.
For more information, you can refer to our previous post – How to Remove Allow Clipboard History Policy in Intune Step by Step Guide.
Need More Help or Have a Technical Question?
JoinLinkedIn page AndTelegram Groupto get step by step guides and news updates. Join usmeEtup pageto participate in User group meetings. Also, JoinWhatsApp CommunicationNityto get the latest news about Microsoft Technologies. We were thereredditas well.
Author
Anoop C Nairhas been a Microsoft MVP for 10 consecutive years from 2015 onwards. He is a Workplace Solutions Architect with over 22+ years of experience in the Workplace technology space. He is a leader of the Community of Bloggers, Speakers, and Local User Groups. The main focus is on Device Management technologies such as SCCM and Intune. He writes about technologies like Intune, SCCM, Windows, Cloud PC, Windows, Entra, Microsoft Security, Career, etc.
News
Berita Teknologi
Berita Olahraga
Sports news
sports
Motivation
football prediction
technology
Berita Technologi
Berita Terkini
Tempat Wisata
News Flash
Football
Gaming
Game News
Gamers
Jasa Artikel
Jasa Backlink
Agen234
Agen234
Agen234
Resep
Cek Ongkir Cargo
Download Film



